 World-leaders in Cryptography: Paul van Oorschot
World-leaders in Cryptography: Paul van Oorschot
ASecuritySite Podcast
Paul is a cryptographer and computer security researcher, and is currently a professor of computer science at Carleton University in Ottawa, Ontario. He previously held a Canada Research Chair in authentication and computer security and is a Fellow of the Royal Society of Canada (FRSC). Along with Alfred Menezes and Scott Vanstone, Paul was a co-author of the Handbook of Applied Cryptography, and the author of Computer Security and the Internet. In 2000, he was awarded The J.W. Graham Medal in Computing Innovation, and a Fellow of the Association for Computing Machinery...
info_outline World-leaders in Cryptography: Craig Costello
World-leaders in Cryptography: Craig Costello
ASecuritySite Podcast
Craig is a Professor of Computer Science at Queensland University of Technology (QUT), who has a special focus on post-quantum cryptography and Zero Knowledge Proofs. He was previously a Principal Researcher at Microsoft Research at Redmond. Craig did his PhD at QUT from 2008 to 2012, and received a Fulbright Scholarship with UC Irvine from 2010 and 2011. In 2015, Craig published details of the FourQ elliptic curve, and which is one of the fastest curves around.
info_outline World-leaders in Cryptography: Kenny Paterson
World-leaders in Cryptography: Kenny Paterson
ASecuritySite Podcast
Kenny is a professor in the Department of Computer Science at ETH Zurich, where he leads the Applied Cryptography Group. He was previously a professor in the Information Security Group at Royal Holloway, University of London. He served as co-chair of the IRTF's research group on Cryptography, CFRG, from 2014 to 2019 and as the Editor-in-Chief for the Journal of Cryptography 2017 to 2020. He was elected as an IACR Fellow in 2017 and was the IACR Distinguished Lecturer in 2025. He obtained his PhD from Royal Holloway in 1993, and his Doctoral Supervisor was...
info_outline World-leaders in Cryptography: Giuseppe Ateniese
World-leaders in Cryptography: Giuseppe Ateniese
ASecuritySite Podcast
Giuseppe is a Professor, Eminent Scholar in the Cybersecurity and CCI Faculty Fellow in the Department of Computer Science and the Department of Cyber Security Engineering at George Mason University. He has advanced many areas of research, including proxy re-encryption, anonymous communication, two-party computation, secure storage, and provable data possession. His current work includes privacy-preserving machine learning and decentralised secure computing based on blockchain technology. He received the NSF CAREER Award for his research on privacy and security, and the Google Faculty...
info_outline World-leaders in Cryptography: Joos Vandewalle
World-leaders in Cryptography: Joos Vandewalle
ASecuritySite Podcast
Joos is a Professor Emeritus with the Department of Electrical Engineering at the Catholic University of Leuven, Belgium. He is one of the most impactful researchers in Computer Science in the World, including in areas of cryptography, secure data communications, data mining and complex systems. His work has led to many areas of impact, including supervising the creators of the Advanced Encryption Standard. He has also worked to simplify the computational complexity of support vector machines, and which involved using a least-squares approach for learning-based classifiers. He has also...
info_outline World-leaders in Cryptography: Jens Groth
World-leaders in Cryptography: Jens Groth
ASecuritySite Podcast
Jens is a Chief Scientist at Nexus, and works in many areas of cryptography including in pairing-based cryptography and Zero-knowledge Proofs (ZKPs). He was previously a Professor of Cryptology at University College, London, and as the Director of Research at DFINITY. In 2016, he published a classic paper of “On the size of pairing-based non-interactive arguments”, and which defines a Zero Knowledge Proof based on pairing-based cryptography. This is now known as Groth16, and is used in many applications, including with Zcash and Tornado Cash. In 2021, he won an IACR Test of Time award for...
info_outline World-leaders in Cryptography: Daniele Micciancio
World-leaders in Cryptography: Daniele Micciancio
ASecuritySite Podcast
Daniele is a professor in the Computer Science and Engineering department at the University of California, San Diego and, in 2019, he was elected as a Fellow of the IACR. His main focus is on the foundations of lattice-based cryptography and its advanced applications, including fully homomorphic encryption. Overall, he has published many classic papers that relate to lattice methods, including working with Chris Peikert on "Trapdoors for lattices", and with Oded Regev on the "Worst-case to average-case reductions based on Gaussian methods". Daniele has also contributed greatly to...
info_outline World-leaders in Cryptography: Gene Tsudik
World-leaders in Cryptography: Gene Tsudik
ASecuritySite Podcast
Gene is a Distinguished and ICS Alumni Professor of Computer Science at the University of California, Irvine (UCI) where he has been since 2000. His research covers areas of security, privacy, and cryptography. From 1991 to 1996, he was a researcher at the IBM Zurich Research Laboratory and then at the Information Science Institute until 2000. He is a Fulbright scholar and a Fellow of the ACM, IEEE, AAAS, and IFIP. From 2009 to 2015, he was the editor-in-chief of the ACM Transactions on Privacy and Security (TOPS). Over the years, Gene has received a number of awards,...
info_outline World-leaders in Technology: Vint Cerf
World-leaders in Technology: Vint Cerf
ASecuritySite Podcast
Vint is seen as one of the founding fathers of the Internet, and along with Robert Kahn, was award the ACM AM Turing Prize - the Nobel Prize of Computer Science - in 2004. Vint contributed to many areas in the creation of the Internet, including writing many RFCs (Requests For Comment) drafts, and in 1974 published the classic paper of "A Protocol for Packet Network Intercommunication" in the IEEE Transactions on Communications. This paper basically defined the IP and TCP protocols that would eventually be used to build the Internet. Along with the A.M. Turing Award, he...
info_outline Panel Discussion: The Quantum clock countdown to Y2Q
Panel Discussion: The Quantum clock countdown to Y2Q
ASecuritySite Podcast
Panel Discussion: The Quantum clock countdown to Y2Q , CEO Scottish Centre of Excellence in Digital Trust and DLT , Founder and CEO ACubed.IT , Founder CyberSeQ J , Senior Researcher Cybernetica Estonia
info_outlineAnd, so, we are moving into one of the greatest changes that we ever see on the Internet, and where we will translate from our existing public key infrastructures towards Post Quantum Cryptography (PQC) methods. At the present time, NIST has approved one key exchange/public key encryption method (Kyber) and three digital signature methods (Dilithium, Falcon and SPHINCS+). The focus will now be on seamless integration, and where we will likely use hybrid methods initially and where we include our existing ECDH method with Kyber, and mix either RSA, ECDSA or EdDSA digital sigatures with Dilithum.
Key exchange is (relatively) straightforward
Overall, Kyber is fairly easy to create a hybrid key exchange method with ECDH, and where we would transmit both the ECC public key and the Kyber public key in the same packet. In fact, Google are already testing its integration in Chrome. With this, our existing key sizes are [here]:
Type Public key size (B) Secret key size (B) Ciphertext size (B)
------------------------------------------------------------------------
P256_HKDF_SHA256 65 32 65
P384_HKDF_SHA384 97 48 97
P521_HKDF_SHA512 133 66 133
X25519_HKDF_SHA256 32 32 32
X448_HKDF_SHA512 56 56 56 Thus, for P256, we have a 32-byte private key (256-bits) and a 65-byte public key (520 bits). Kyber 512 increase the key size of 1,632 bytes for the private key, and 800 bytes (6,400 bits) for the public key:
Type Public key size (B) Secret key size (B) Ciphertext size (B)
------------------------------------------------------------------------
Kyber512 800 1,632 768
Kyber738 1,184 2,400 1,088
Kyber1024 1,568 3,168 1,568 Thus, to use a hybrid key exchange method, we would include the ECC public key and the Kyber512 public key and thus have a packet which contains 832 bytes. This is smaller than the 1,500 byte limit for an IP packet and thus requires only one packet to send the public key from Bob to Alice (and vice-versa). A Hybrid method is defined here:
https://asecuritysite.com/pqc/circl_hybrid
and a test run is:
Method: Kyber512-X25519
Public Key (pk) = 3BF9B5BB236AD036BA65B1B532E11927E20269D3CE74009E6C085F0D901F5CC9 (first 32 bytes)
Private key (sk) = B96B644DE170BA19266AF32BFA4B3B22A4917888A2EE785C701B7252D6308573 (first 32 bytes)
Cipher text (ct) = 0E54F37E171768318B45FD27FBDB08B33CD2204142C4B925BB395DA93AE26EA7 (first 32 bytes)
Shared key (Bob): C0B27940D588EE1D0F8348F169BA04A48E0E7FA7DE5B8A091D5D1B59E70D577EEAC4180B076595B2EFCCE96E2271EEA3B20228FC3FD5B63114D32E9D20D9A2F2
Shared key (Alice): C0B27940D588EE1D0F8348F169BA04A48E0E7FA7DE5B8A091D5D1B59E70D577EEAC4180B076595B2EFCCE96E2271EEA3B20228FC3FD5B63114D32E9D20D9A2F2
Length of Public Key (pk) = 832 bytes
Length of Secret Key (sk) = 1664 bytes
Length of Cipher text (ct) = 800 bytes Digital Signatures and PKI is not so easy
But, what will happen with the next part of the process, and where we need to digitally sign something with a private key and then prove with the public key? This is an important element in HTTPs, and where ECDH is used to exchange the symmetric key, and then digital signatures are used to verify the identity of the server. For this, we use digital certificates (X.509), and which contain the public key of the entity and which has been signed by a trusted entity (Trent).
Well, at the present time, it is not quite clear yet, and a new IETF draft perhaps gives some insights [here]:
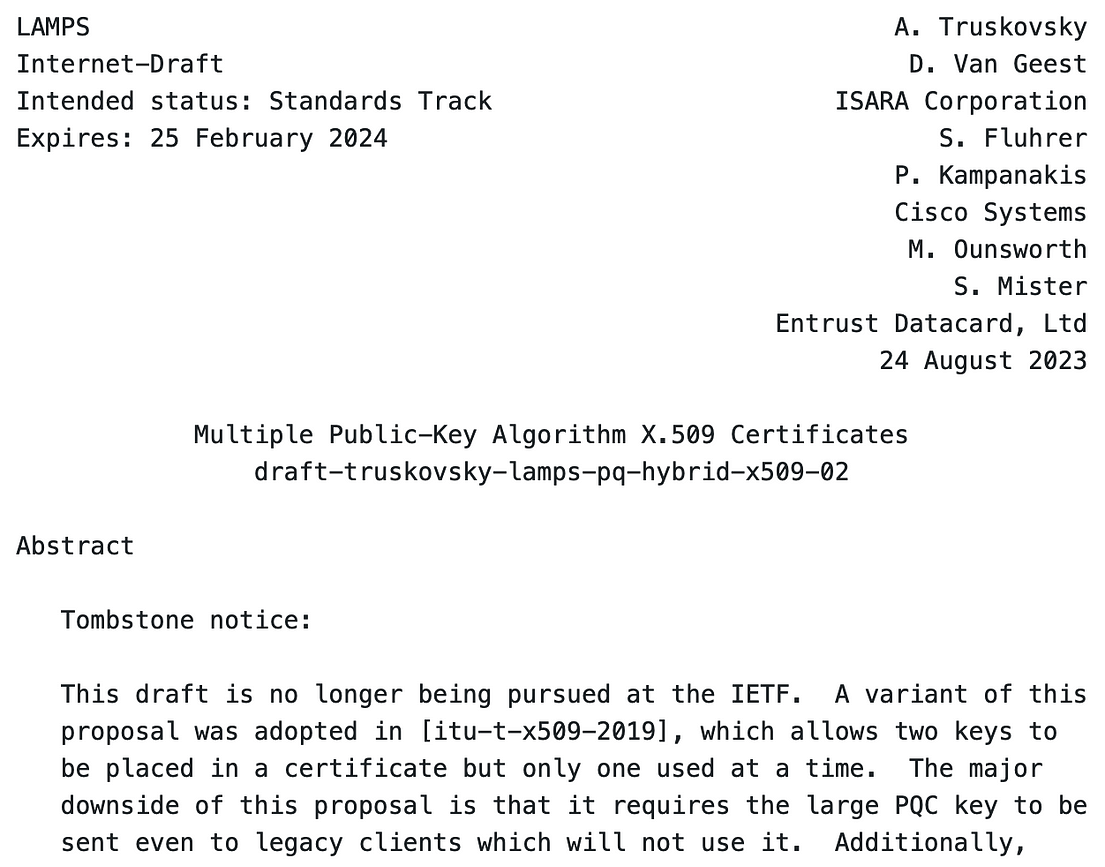
The draft outlines how we could include two public keys in the same certificate: such as an ECC or RSA public key and a PQC public key. Unfortunately, it has been given a “Tombstone notice”, which means it will not progress. The reason for this is that it adds a PQC key — no matter if the host actually wants (or uses) it. Along with this, it does not give a mechanism for coping with two signatures on a method (with a traditional one and a PQC one), and where it is not possible to detect where one of the signatures has been removed — a stripping attack.
Public key sizes for Dilithum
Like it or not, the days of small public key sizes are coming to an end. In ECC, for NIST P256, we have a 32-byte (256 bit) private key, and a 64-byte (512-bit) public key. For Ed25519, we use Curve 25519, and which reduces the public key to ust 32 bytes (256 bits).
For RSA 2K, we have a 256-byte private key (2,048 bits), and a 256-byte public key (2,048 bits). The equivalent security for Dililithum is Dililithum2, and which gives a much larger private key of 2,528 bytes (20,224 bits) and a public key of 1,312 bytes (10,496 bits). The Dilithium public key is thus over 20 times larger than the ECC key. This could be a major overhead in communication systems, and where more than one data packet would have to be sent in order to transmit the public key.
Method Public key size Private key size Signature size Security level
------------------------------------------------------------------------------------------------------
Crystals Dilithium 2 (Lattice) 1,312 2,528 2,420 1 (128-bit) Lattice
Crystals Dilithium 3 1,952 4,000 3,293 3 (192-bit) Lattice
Crystals Dilithium 5 2,592 4,864 4,595 5 (256-bit) Lattice
Falcon 512 (Lattice) 897 1,281 690 1 (128-bit) Lattice
Falcon 1024 1,793 2,305 1,330 5 (256-bit) Lattice
Sphincs SHA256-128f Simple 32 64 17,088 1 (128-bit) Hash-based
Sphincs SHA256-192f Simple 48 96 35,664 3 (192-bit) Hash-based
Sphincs SHA256-256f Simple 64 128 49,856 5 (256-bit) Hash-based
RSA-2048 256 256 256
ECC 256-bit 64 32 256 A hybrid scheme is defined here:
https://asecuritysite.com/pqc/circl_dil2
For our existing signatures, we have:
Method Public key size (B) Private key size (B) Signature size (B) Security level
------------------------------------------------------------------------------------------------------
Ed25519 32 32 64 1 (128-bit) EdDSA
Ed448 57 57 112 3 (192-bit) EdDSA
ECDSA 64 32 48 1 (128-bit) ECDSA
RSA-2048 256 256 256 1 (128-bit) RSA And in using a hybrid approach, we increase the signature size of 64 bytes or Ed25519 to 2,484 bytes — a 38-fold increase in size:
Method Public key size Private key size Signature size Security level
------------------------------------------------------------------------------------------------------
Crystals Dilithium2-X25519 2,560 1,344 2,484 1 (128-bit) Lattice
Crystals Dilithium3-X25519 4,057 2,009 3,407 3 (192-bit) Lattice
Crystals Dilithium 2 (Lattice) 1,312 2,528 2,420 1 (128-bit) Lattice
Crystals Dilithium 3 1,952 4,000 3,293 3 (192-bit) Lattice
Crystals Dilithium 5 2,592 4,864 4,595 5 (256-bit) Lattice
Falcon 512 (Lattice) 897 1,281 690 1 (128-bit) Lattice
Falcon 1024 1,793 2,305 1,330 5 (256-bit) Lattice
Sphincs SHA256-128f Simple 32 64 17,088 1 (128-bit) Hash-based
Sphincs SHA256-192f Simple 48 96 35,664 3 (192-bit) Hash-based
Sphincs SHA256-256f Simple 64 128 49,856 5 (256-bit) Hash-based And, so, what about using SPHINCS+? That has a 32-byte public key. The downside is that Sphincs SHA256–128f requires a 17,088-byte signature. This would also overload the communication channel and require over 11 packets to send a single signature to prove the identity of a Web site. It is highly unlikely that SPHINCS+ will be used to replace RSA and ECC signatures in ECDH, but where it would be used in applications that did not have a communications channel.
Conclusions
And, so, the double public key draft has been sent back, and we are awaiting the next iteration.
Learn more about PQC here:
