Bill Buchanan - Test-of-Time (ToT) for Research Papers: Some Papers Rocket, Some Papers Crash, and But Most Never Go Anywhere
Release Date: 09/03/2023
 World-leaders in Cryptography: Leslie Lamport
World-leaders in Cryptography: Leslie Lamport
ASecuritySite Podcast
Please excuse the poor quality of my microphone, as the wrong microphone was selected. In research, we are all just building on the shoulders of true giants, and there are few larger giants than Leslie Lamport — the creator of LaTeX. For me, every time I open up a LaTeX document, I think of the work he did on creating LaTeX, and which makes my research work so much more productive. If I was still stuck with Microsoft Office for research, I would spend half of my time in that horrible equation editor, or in trying to integrate the references into the required format, or in...
info_outline World-leaders in Cryptography: Daniel J Bernstein
World-leaders in Cryptography: Daniel J Bernstein
ASecuritySite Podcast
Daniel J Bernstein (djb) was born in 1971. He is a USA/German citizen and a Personal Professor at Eindhoven University of Technology and a Research Professor at the University of Illinois at Chicago. At the tender age of 24 — in 1995 — he, along with the Electronic Frontier Foundation — brought a case against the US Government related to the protection of free speech (Bernstein v. United States: ). It resulted in a ruling that software should be included in the First Amendment. A core contribution is that it has reduced government regulations around cryptography. It was a sign of the...
info_outline World-leaders in Cryptography: Jan Camenisch
World-leaders in Cryptography: Jan Camenisch
ASecuritySite Podcast
Jan is the CTO and a Cryptographer at DFINITY, and, since 1998, he has consistently produced research outputs of rigour, novelty and sheer brilliance [here]. He was recently awarded the Levchin Prize at Real World Crypto 2024 - along with Anna Lysyanskaya. Jan’s research core happened when he was hosted in the IBM Zurich Research Lab, but has since moved to DFINITY, and is still producing research outputs that are some of the best in the whole of the computer science research area. He has published over 140 widely cited papers and has been granted around 140 patents. Jan has also received...
info_outline An Interview with Ted Miracco
An Interview with Ted Miracco
ASecuritySite Podcast
Ted Miracco is the CEO of Approov and which is Scottish/US company that is headquartered in Edinburgh. Miracco has over 30 years of experience in cybersecurity, defence electronics, RF/microwave circuit design, semiconductors and electronic design automation (EDA). He co-founded and served as CEO of Cylynt, which focuses on intellectual property and compliance protection
info_outline World-leaders in Cybersecurity: Troy Hunt
World-leaders in Cybersecurity: Troy Hunt
ASecuritySite Podcast
Troy is a world-leading cybersecurity professional. He created and runs the Have I Been Pwned? Web site, and which contains details of the most significant data breaches on the Internet. Along with this, he has developed other security tools, such as ASafaWeb, which automated the security analysis of ASP.NET Web sites. Troy is based in Australia and has an extensive blog at
info_outline The Greatest Step Change in Cybersecurity Ever! Welcome to the New and Scary World of Generative AI and Cybersecurity
The Greatest Step Change in Cybersecurity Ever! Welcome to the New and Scary World of Generative AI and Cybersecurity
ASecuritySite Podcast
This is Day 0 of a new world of cybersecurity. Everything changes from here. There will be a time before Generative AI (GenAI) in cybersecurity and a time after it. Over the last two years, GenAI has come on leaps and bounds, and where it once suffered from hallucinations, took racist and bigoted approaches, and often was over-assertive, within ChatGPT 4.5, we see the rise of a friendly and slightly submissive agent, and that is eager to learn from us. This LLM (Large Language Model) approach thus starts to break down the barriers between humans and computers and brings the opportunity to gain...
info_outline Towards the Memex: All Hail The Future Rulers of our World
Towards the Memex: All Hail The Future Rulers of our World
ASecuritySite Podcast
And, so George Orwell projected a world where every single part of our lives was monitored and controlled by Big Brother. Arthur C Clark outlined the day when machines focused solely on a goal — even if it was to the detriment of human lives. And, Isaac Asimov outlined a world where machines would have to be programmed with rules so that they could not harm a human. The Rise of the Machine With the almost exponential rise in the power of AI, we are perhaps approaching a technological singularity — a time when technological growth becomes uncontrollable and irreversible, and which can have...
info_outline World-leaders in Cryptography: Marty Hellman (March 2024)
World-leaders in Cryptography: Marty Hellman (March 2024)
ASecuritySite Podcast
This seminar series runs for students on the Applied Cryptography and Trust module, but invites guests from students from across the university. Martin is one of the co-creators of public key encryption, and worked alongside Whitfield Diffie in the creation of the widely used Diffie-Hellman method. In 2015, he was presented with the ACM Turing Award (the equivalent of a Nobel Prize in Computer Science) for his contribution to computer science. He is currently a professor emeritus at Stanford University. https://engineering.stanford.edu/node/9141/printable/print
info_outline World-leaders in Cryptography: Vincent Rijmen (March 2024)
World-leaders in Cryptography: Vincent Rijmen (March 2024)
ASecuritySite Podcast
Vincent Rijmen is one of the co-creators of the NIST-defined AES standard (also known as Rijndael). He also co-designed the WHIRLPOOL hashing method, along with designing other block ciphers, such as Square and SHARK. In 2002, Vincent was included in the Top 100 innovators in the world under the age of 35, and, along with Joan Daemen, was awarded the RSA Award for Excellence in Mathematics. He recently joined Cryptomathic as a chief cryptographer, and also holds a professor position (gewoon hoogleraar) at K.U.Leuven, and adjunct professorship at the University of Bergen, Norway. His paper on...
info_outline World-leaders in Cryptography: Whitfield Diffie
World-leaders in Cryptography: Whitfield Diffie
ASecuritySite Podcast
Whitfield Diffie is one of the greatest Computer Scientists ever. He - along with Marty Hellman - was one of the first to propose the usage of public key encryption and co-created the Diffie-Hellman (DH) key exchange method. Overall, the Diffie-Hellman method is still used in virtually every Web connection on the Internet, and has changed from using discrete log methods to elliptic curve methods. In 2015, Whitfield was also awarded the ACM Turing Prize - and which is the Nobel Prize equivalent in Computer Science. In this on-line talk he meets with Edinburgh Napier University students,...
info_outlineIn research, the publishing of high-quality papers is often critical for the development of a research career:
“I am an academic. It’s publish or perish.” Daniel J Bernstien.
But often we measure the work in terms of quality rather than quantity. One high-quality research paper is probably worth more than the millions of papers published in predatory journals. A great researcher should be able to measure the quality of their work by the known impact and contribution of their research papers, and not by citation count or journal impact factor. In fact, review papers often contribute little to the development of new methods, but are some of the most highly cited papers.
A research paper thus has a life. Authors might have a dream that their work is going to fundamentally change a given field, but it ends up never being read much and withers. Overall, most papers just bob along with a few citations in a year, and where you are lucky if you get more than 10 citations. An academic often follow the impact of their papers on Google Scholar, and which can give you an idea of whether their work is rising or on the wain. If you are interested, here’s mine showing a nice exponential rise over the past few years:

Some papers might rocket with many initial citations, and where researchers cite them heavily, but then either the research area just dies off with a lack of interest, or problems are found with it. Isogenies within post-quantum methods is one example of this, and where a single crack on SIDH (Supersinglar Isogeny Diffie-Hellman) stopped some of the advancements in the field [here]:
Up to that point, isogenies were the poster child and the great hope for competing with lattice methods. While they were still slow, researchers were gearing up their research to address many of their performance weakneses. They were much loved, as they used elliptic curves, but one paper stalled the isogeny steam train. I do believe they will return strong, but it will take a while to recover from such a serious crack. Cryptography is often about reputation, and a single crack can bring the whole method down.
Other papers, though, can be slow burners. The core papers in ECC (Elliptic Curve Cryptography), for example, did not take off for a few years after the work was published. When Neal Koblitz published his paper on “Elliptic curve cryptosystems” in 1987, it was hardly cited, and few people picked up the potential to replace RSA signatures. In 1997 (10 years after the publication of the paper), it is still only achieved 41 citations. But things really took off around 2005, and especially when Satoshi Nakamoto adopted ECC for Bitcoin around 2009. It now sits at nearly 400 citations per year, and where ECDSA and EdDSA have made a significant impact in replacing our cumbersome RSA methods:

Test-of-Time (ToT) Award
Now Chris Peikert, Brent Waters, and Vinod Vaikuntanathan (Via-kun-tan-athan) have been awarded the International Association for Cryptologic Research (IACR) Test-of-Time (ToT) Award for a paper entitled “A Framework for Efficient and Composable Oblivious Transfer” and presented at the Crypto 2008 conference [here][1]:

Overall, the Test-of-Time Awards is awarded to papers published over 15 years ago, with the three IACR general conferences (Eurocrypt, Crypto and Asiacrypt).
The developed framework integrates “universal composability” and which provides strong security properties. Basically, a protocol P1 is secure if another protocol (P2) emulates P1, and where it is not possible to tell the two apart. It introduced a simple method of “dual-mode cryptosystem”.
The work has been fundamental in creating Oblivious Transfer protocols, and which are used in Multi-Party Computation (MPC). A great advancement of the paper is in the usage of Learning with Errors (LWE) — and which is now used within lattice cryptography methods. The paper has since laid a foundation for lattice cryptography.
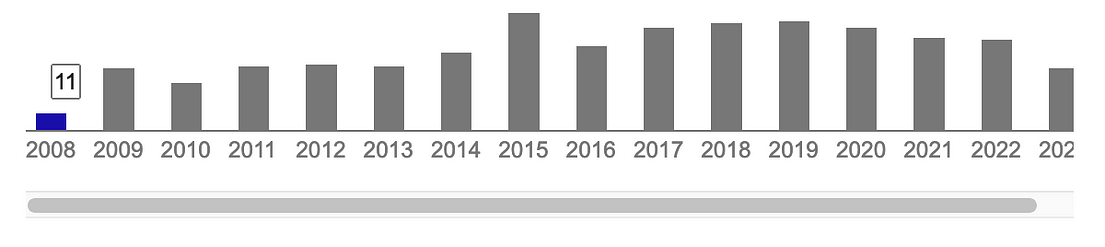
As with the ECC method, the paper was a slow-burner [here] with only 11 citations in 2008, but rose to more than 10 times that number:
MPC
So, let’s see if we can build a model where we can securely distribute value and then get our nodes to perform the result of a calculation. None of the nodes should be able to compute the result without the help of others, and where Trent is trusted to distribute the inputs, watch the broadcasts, and then gather the results. For this, we can use Shamir secret shares, and where a value can be split into t-from-n shares and where we need t shares to rebuild our value.
So, we could distribute a 2-from-3 to Bob, Alice and Eve, and they Bob and Alice, or Alice and Eve, could rebuild the value back again. So let’s say we have two values: x and y, and we want to compute x×y. We then initially start with n parties, and where we define a threshold of t (the minimum number of shares required to rebuild any value. Initially, Trent (the trusted dealer) splits the input values of x and y into shares:
Sharesx=x1,x2,…xn
Sharesy=y1,y2,…yn
Next, Trent sends one share of each to each of the nodes, such as xi and yi to node i. Each node then must gather at least t shares for the nodes, and then aim to add to its own share. Each node is then able to rebuild the values of x and y, and then compute x×y. Trent then receives all the results back and makes a judgement on the consensus. If we have 12 nodes, then if there are at least eight nodes that are fair, the result will be the correct one.
Here is the code [here]:
package main
import (
"fmt"
"github.com/codahale/sss"
"os"
"strconv"
"encoding/hex"
)
func mult(subset1 map[byte][]byte, subset2 map[byte][]byte) int {
a_reconstructed := string(sss.Combine(subset1))
b_reconstructed := string(sss.Combine(subset2))
a,_ := strconv.Atoi(a_reconstructed)
b,_ := strconv.Atoi(b_reconstructed)
res:=a*b;
return(res)
}
func add(subset1 map[byte][]byte, subset2 map[byte][]byte) int {
a_reconstructed := string(sss.Combine(subset1))
b_reconstructed := string(sss.Combine(subset2))
a,_ := strconv.Atoi(a_reconstructed)
b,_ := strconv.Atoi(b_reconstructed)
res:=a+b;
return(res)
}
func sub(subset1 map[byte][]byte, subset2 map[byte][]byte) int {
a_reconstructed := string(sss.Combine(subset1))
b_reconstructed := string(sss.Combine(subset2))
a,_ := strconv.Atoi(a_reconstructed)
b,_ := strconv.Atoi(b_reconstructed)
res:=a-b;
return(res)
}
func get_shares(shares map[byte][]byte , k byte) map[byte][]byte {
subset := make(map[byte][]byte, k)
for x, y := range shares {
fmt.Printf("Share:\t%d\t%s ",x,hex.EncodeToString(y))
subset[x] = y
if len(subset) == int(k) {
break
}
}
fmt.Printf("\n")
return(subset)
}
func main() {
a:= "10"
b:="11"
n1:=5
k1:=3
argCount := len(os.Args[1:])
if (argCount>0) {a = (os.Args[1])}
if (argCount>1) {b = (os.Args[2])}
if (argCount>2) {k1,_ = strconv.Atoi(os.Args[3])}
if (argCount>3) {n1,_ = strconv.Atoi(os.Args[4])}
n := byte(n1)
k := byte(k1)
fmt.Printf("a:\t%s\tb: %s\n\n",a,b)
fmt.Printf("Policy. Any %d from %d\n\n",k1,n1)
if (k1>n1) {
fmt.Printf("Cannot do this, as k greater than n")
os.Exit(0)
}
shares1, _:= sss.Split(n, k, []byte(a))
shares2, _:= sss.Split(n, k, []byte(b))
a_subset:=get_shares(shares1,k)
b_subset:=get_shares(shares2,k)
res1:=mult(a_subset, b_subset)
res2:=add(a_subset, b_subset)
res3:=sub(a_subset, b_subset)
fmt.Printf("\na*b= %d\n",res1)
fmt.Printf("a+b= %d\n",res2)
fmt.Printf("a-b= %d\n",res3)
} A sample run is [here]:
a: 10 b: 11
Policy. Any 3 from 5
Share: 5 fe87 Share: 1 8bd2 Share: 2 16c7
Share: 2 e47a Share: 3 db58 Share: 4 1a9b
a*b= 110
a+b= 21
a-b= -1 and:
a: 9999 b: 9998
Policy. Any 3 from 6
Share: 1 968ada76 Share: 2 44fc9b0c Share: 3 eb4f7843
Share: 4 6d4bf67a Share: 5 1cbaf095 Share: 6 3ef251e3
a*b= 99970002
a+b= 19997
a-b= 1 Conclusions
The paper by Peikert, Vaikuntanathan, and Waters laid the ground for some many areas, including MPC and lattice-based cryptography. After 15 years since it has been published, it has been referenced over 821 times, and is a highly recommended read. And, so, don’t measure the initial impact of a paper by the number of citations it receives after a year or two — as its time may yet be to come.
For ECRs … have faith in your work … if you keep your focus, your work will get noticed. If not, you perhaps have the wrong focus or in the wrong field.
References
[1] Peikert, Chris, Vinod Vaikuntanathan, and Brent Waters. “A framework for efficient and composable oblivious transfer.” Annual international cryptology conference. Berlin, Heidelberg: Springer Berlin Heidelberg, 2008.
[2] Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of computation, 48(177), 203–209.
