 World-leaders in Cryptography: Paul van Oorschot
World-leaders in Cryptography: Paul van Oorschot
ASecuritySite Podcast
Paul is a cryptographer and computer security researcher, and is currently a professor of computer science at Carleton University in Ottawa, Ontario. He previously held a Canada Research Chair in authentication and computer security and is a Fellow of the Royal Society of Canada (FRSC). Along with Alfred Menezes and Scott Vanstone, Paul was a co-author of the Handbook of Applied Cryptography, and the author of Computer Security and the Internet. In 2000, he was awarded The J.W. Graham Medal in Computing Innovation, and a Fellow of the Association for Computing Machinery...
info_outline World-leaders in Cryptography: Craig Costello
World-leaders in Cryptography: Craig Costello
ASecuritySite Podcast
Craig is a Professor of Computer Science at Queensland University of Technology (QUT), who has a special focus on post-quantum cryptography and Zero Knowledge Proofs. He was previously a Principal Researcher at Microsoft Research at Redmond. Craig did his PhD at QUT from 2008 to 2012, and received a Fulbright Scholarship with UC Irvine from 2010 and 2011. In 2015, Craig published details of the FourQ elliptic curve, and which is one of the fastest curves around.
info_outline World-leaders in Cryptography: Kenny Paterson
World-leaders in Cryptography: Kenny Paterson
ASecuritySite Podcast
Kenny is a professor in the Department of Computer Science at ETH Zurich, where he leads the Applied Cryptography Group. He was previously a professor in the Information Security Group at Royal Holloway, University of London. He served as co-chair of the IRTF's research group on Cryptography, CFRG, from 2014 to 2019 and as the Editor-in-Chief for the Journal of Cryptography 2017 to 2020. He was elected as an IACR Fellow in 2017 and was the IACR Distinguished Lecturer in 2025. He obtained his PhD from Royal Holloway in 1993, and his Doctoral Supervisor was...
info_outline World-leaders in Cryptography: Giuseppe Ateniese
World-leaders in Cryptography: Giuseppe Ateniese
ASecuritySite Podcast
Giuseppe is a Professor, Eminent Scholar in the Cybersecurity and CCI Faculty Fellow in the Department of Computer Science and the Department of Cyber Security Engineering at George Mason University. He has advanced many areas of research, including proxy re-encryption, anonymous communication, two-party computation, secure storage, and provable data possession. His current work includes privacy-preserving machine learning and decentralised secure computing based on blockchain technology. He received the NSF CAREER Award for his research on privacy and security, and the Google Faculty...
info_outline World-leaders in Cryptography: Joos Vandewalle
World-leaders in Cryptography: Joos Vandewalle
ASecuritySite Podcast
Joos is a Professor Emeritus with the Department of Electrical Engineering at the Catholic University of Leuven, Belgium. He is one of the most impactful researchers in Computer Science in the World, including in areas of cryptography, secure data communications, data mining and complex systems. His work has led to many areas of impact, including supervising the creators of the Advanced Encryption Standard. He has also worked to simplify the computational complexity of support vector machines, and which involved using a least-squares approach for learning-based classifiers. He has also...
info_outline World-leaders in Cryptography: Jens Groth
World-leaders in Cryptography: Jens Groth
ASecuritySite Podcast
Jens is a Chief Scientist at Nexus, and works in many areas of cryptography including in pairing-based cryptography and Zero-knowledge Proofs (ZKPs). He was previously a Professor of Cryptology at University College, London, and as the Director of Research at DFINITY. In 2016, he published a classic paper of “On the size of pairing-based non-interactive arguments”, and which defines a Zero Knowledge Proof based on pairing-based cryptography. This is now known as Groth16, and is used in many applications, including with Zcash and Tornado Cash. In 2021, he won an IACR Test of Time award for...
info_outline World-leaders in Cryptography: Daniele Micciancio
World-leaders in Cryptography: Daniele Micciancio
ASecuritySite Podcast
Daniele is a professor in the Computer Science and Engineering department at the University of California, San Diego and, in 2019, he was elected as a Fellow of the IACR. His main focus is on the foundations of lattice-based cryptography and its advanced applications, including fully homomorphic encryption. Overall, he has published many classic papers that relate to lattice methods, including working with Chris Peikert on "Trapdoors for lattices", and with Oded Regev on the "Worst-case to average-case reductions based on Gaussian methods". Daniele has also contributed greatly to...
info_outline World-leaders in Cryptography: Gene Tsudik
World-leaders in Cryptography: Gene Tsudik
ASecuritySite Podcast
Gene is a Distinguished and ICS Alumni Professor of Computer Science at the University of California, Irvine (UCI) where he has been since 2000. His research covers areas of security, privacy, and cryptography. From 1991 to 1996, he was a researcher at the IBM Zurich Research Laboratory and then at the Information Science Institute until 2000. He is a Fulbright scholar and a Fellow of the ACM, IEEE, AAAS, and IFIP. From 2009 to 2015, he was the editor-in-chief of the ACM Transactions on Privacy and Security (TOPS). Over the years, Gene has received a number of awards,...
info_outline World-leaders in Technology: Vint Cerf
World-leaders in Technology: Vint Cerf
ASecuritySite Podcast
Vint is seen as one of the founding fathers of the Internet, and along with Robert Kahn, was award the ACM AM Turing Prize - the Nobel Prize of Computer Science - in 2004. Vint contributed to many areas in the creation of the Internet, including writing many RFCs (Requests For Comment) drafts, and in 1974 published the classic paper of "A Protocol for Packet Network Intercommunication" in the IEEE Transactions on Communications. This paper basically defined the IP and TCP protocols that would eventually be used to build the Internet. Along with the A.M. Turing Award, he...
info_outline Panel Discussion: The Quantum clock countdown to Y2Q
Panel Discussion: The Quantum clock countdown to Y2Q
ASecuritySite Podcast
Panel Discussion: The Quantum clock countdown to Y2Q , CEO Scottish Centre of Excellence in Digital Trust and DLT , Founder and CEO ACubed.IT , Founder CyberSeQ J , Senior Researcher Cybernetica Estonia
info_outlineI do what I do because of one company … IBM. Why? Because in the 1970s, I got into computers, with a ZX81 (1KB of RAM) and a Dragon 32 (32 KB of RAM). They were very much home computers, and where you would rush out and buy the latest computer magazine, and then spend a happy evening entering some BASIC code that made a cursor move across the screen using the IJLM keys. If you were very lucky you would manage to save it to a cassette — that could take over ten minutes to save a simple program — only to get an error at the end. I was hooked!
But, at work, we had a DEC VAX minicomputer, and which cost a fortune to buy and maintain (even in those days). This mini ran typically Pascal, and I remember running labs for students, and where they all decided to compile their program at the same time, and 30 minutes later, some of them would get their errors, and have to compile it again. Basically, every lab ended with me saying, “Sorry about that.”

The VAX, though, was not designed to support 25 students compiling their program at the same time … it was a batch processing machine and wanted to be given jobs that it could run whenever it had time. It basically came from the days when you handed in your punch cards (containing either FORTRAN if you were an engineer or COBOL if you were more business-focused) to someone with a white coat, and then came back the next week with a printed output with green lined paper.
But, just in time, the IBM PC arrived, and it was heavy but beautiful. So, as many in my department pushed for the VAX, but pushed for the PC for our labs. With their clock speed of 4.7 MHz, and 640KB of memory, I went ahead and bought a batch for a new PC lab. In those days there were no network switches, so they all connected with coaxial cable and had T-pieces to connect to the shared Ethernet bus. My logic was that we were paying around £20K for maintenance on the VAX, and where we could buy 20 £1K PC clones for the same cost. But, we’d have to maintain them. And, it worked. It freed us, and allowed us to run the classic Turbo Pascal (and Turbo C):
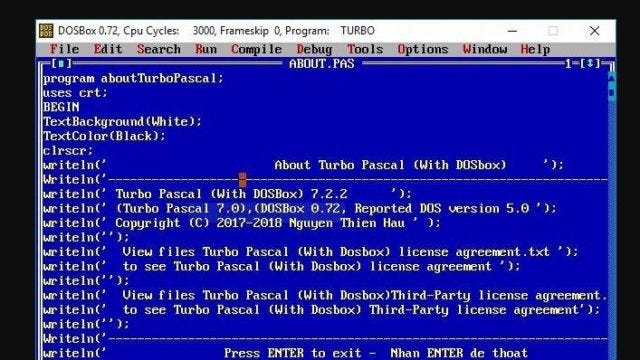
Our student could now bring in their 5-inch floppy disks and save their programs for later use. And the size of the hard disk? 20MB!
And, so, it is to IBM that we turn in starting the PC revolution, and today is the 100th anniversary of the IBM name — and first defined on 15 Feb 1924.
